Posted on
2022-04-13
by
Matt Strahan
in
Volkis News
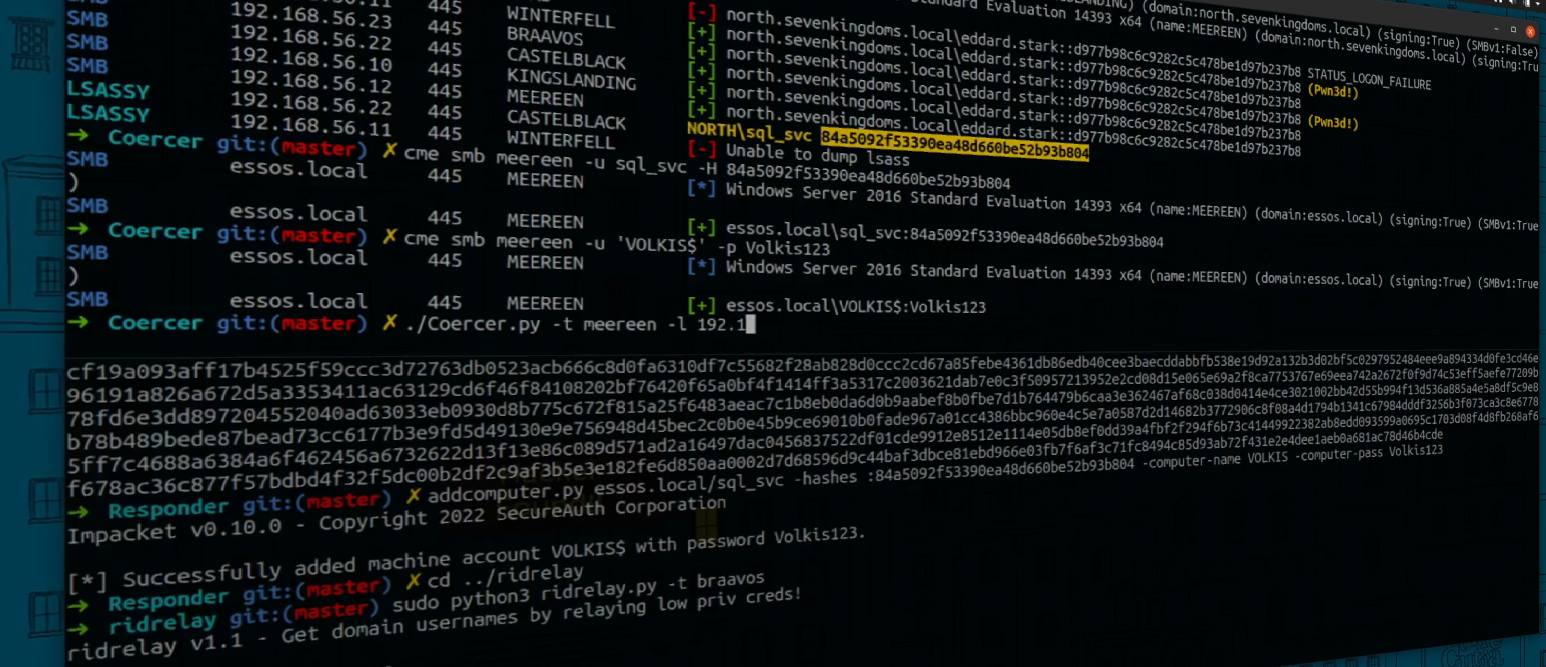
When building a cyber security company there’s a question we have to keep front of mind at all times. What value do we bring as a company? It’s one thing to just say “yes of course we provide value as a company” but for me I’ve tried to make an actual list. I’ve put up the results of this up in a new handbook page.
This exercise is more than just a bit of a boost for our egos. Rather, it’s a genuine component of the consulting model - of the business model that Volkis fits into. Whenever we have an engagement, there are three parties that come into play. They are the client, the consultancy, and the consultants themselves. The value of the consultants’ time is obvious: they perform the work. They find the security vulnerabilities in the systems that are being tested or find the ways the system might not be up to spec.
Why would the client not just contract someone out directly or employ their own pentester? If we don’t provide actual value then what’s the point? Thinking about this question directly has helped me solidify in my mind what we need to do well as a company and helped build our business model.