Posted on
2024-04-30
by
Matt Strahan
in
Business Security
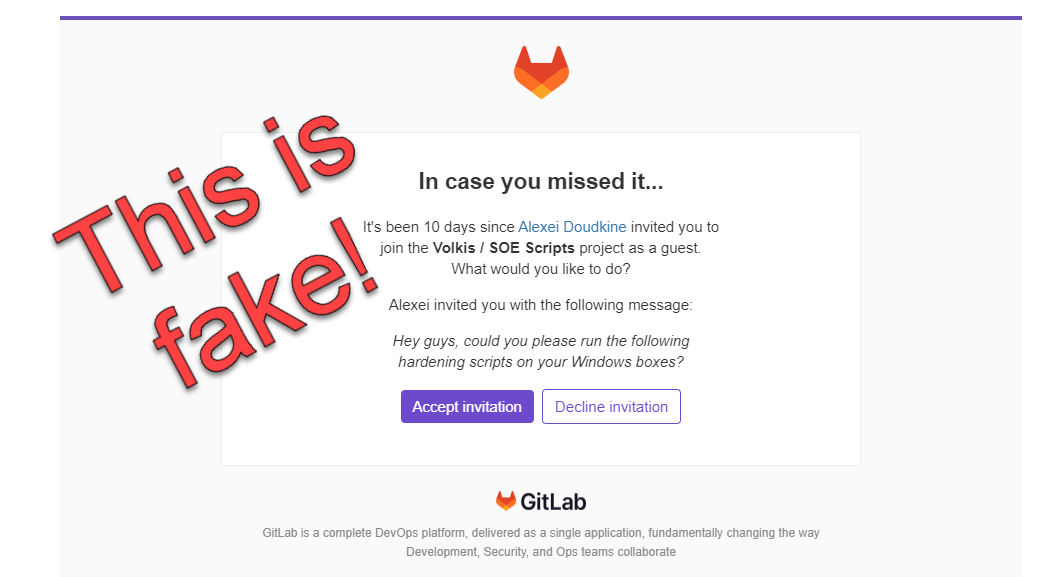
I was working on a penetration test for a gym company a while ago and found a vulnerability. When looking at the profile I found you could change the number in the URL and view other profiles. “Unfortunately” you couldn’t change the other user’s password, but wait! There’s a forgotten password function and I’m able to change the user’s email address! How about I just change the email address, submit the forgotten password page, and then…great I’ve got access to the account!
For the pentesters who are reading this, this is not a particularly interesting story. It’s just the exploitation of a stock standard IDOR vulnerability using a pretty well known technique. They’d put the recommendation to require the user’s password for changing email address and oh don’t forget to fix the IDOR.
But for some reason this story was rolling around in my head not long ago and it made me think. For this company the email address ended up being just another way of authenticate. In terms of authentication it was equivalent to just having the username and password. In other words, you could have either a username and password to access the account or access to the email.
We all kind of know this when we think it through, but did the company treat email this way? Did they treat access to email as a method of authentication in the same way as a password?