
Posted on 2023-04-20 by Alexei Doudkine in Industry
You’re probably here because, like many others, you’ve gone out looking for offensive cyber-security services only to be give a bunch of buzz words that don’t really describe what they are or what they mean for you. Fear not; in this post I hope to demystify the most common ones, in simple terms and explain the benefits and shortcomings of each. I’ll also give a few examples of when each one would be useful.
It’s important to remember that even within the infosec industry, there can be disagreements about what a specific service should entail, be it penetration testing or red team, or vulnerability assessment. Also, as the industry evolves, so do the services. If you’re ever in doubt about what a provider does for each service, check their Service Catalogue if they have one, or just ask.
Penetration Test
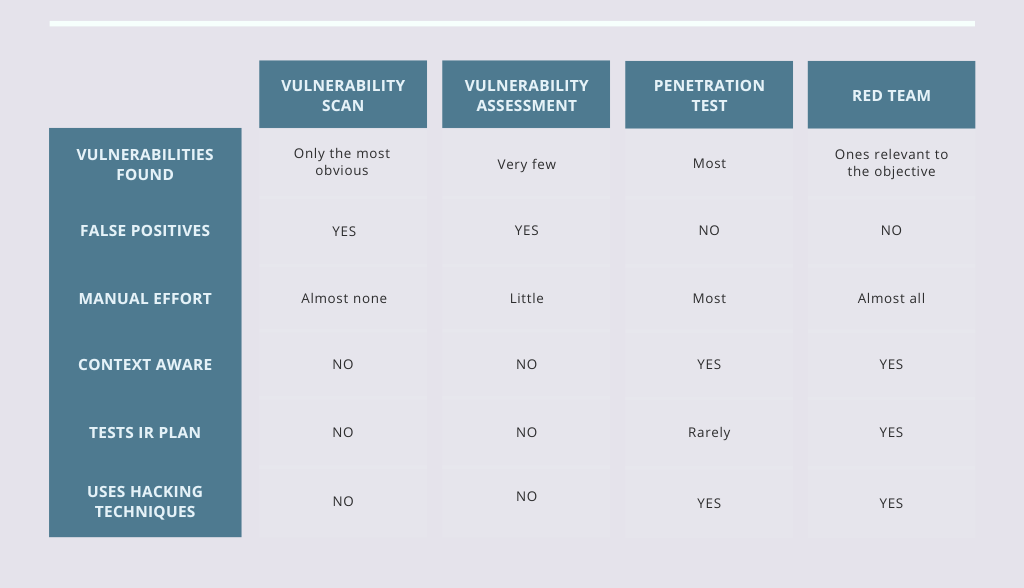
Of all offensive security style services, penetration testing is probably the most common. The goal of a penetration test (sometimes shortened to pentest or pen test) is simple; find as many vulnerabilities (vulns) in the given scope as possible. We deem a vulnerability as anything that can realistically have a negative impact to an organisation. Sometimes it’s as complex as finding a flaw in a random number generator and abusing it to impersonate the CEO, other times it’s just “this page has sensitive information but no access control”. Both are vulnerabilities.
In a pentest, vulnerabilities are exploited (that is, abused for the hacker’s gain) for multiple reasons:
- To identify it in the first place. Sometimes its easier to send a payload and see how the system responds. If it responds in a certain way, it could be a vuln;
- To eliminate false positives;
- To understand the impact that a vuln can have on the organisation.
Pentesters use the same hacking tools and techniques that actual attackers use to try and mimic what they would do before they have a chance, allowing you to secure your organisation from those same techniques. This is done almost entirely manually. Yes, tools and scanners are used, but they are driven by a human, using their intuition, experience and, importantly, context to find the most impactful vulnerabilities.
When to get a pentest
If you want to quickly discover vulnerabilities that real adversaries could use against your organisation, get a pentest. You should receive consultation and a report that explains what vulns were found and how to fix them. A lot more goes into a report, so if you’re interested, check out our Sample Penetration Test Report.
Be careful of scammers
Sadly, there are firms out there that will sell a vulnerability scan and call it a pentest. Watch out for those. If you see something call an “Automated Penetration Test”, that’s a huge red flag. Stay away. If the pentest was mostly automated, that’s not a pentest, it’s a vulnerability scan.
Red Team engagements
A Red Team engagement (or “Red Teaming”) is as close to a real world hack on your organisation as you’re legally going to get. It is usually a wide or completely open scope of the entire organisation allowing the Red Team (attackers) to find a way in by any means necessary, including social engineering or physical intrusion efforts.
The goal of a Red Team is to obtain a primary business objective (or objectives). I say business objective because it should be something related to business activities. A good objective might be “Show that you can shut down the refinery.” In contrast, a bad objective might be, “Get Domain Admin privileges,” because that doesn’t show any real impact to the business. The Red Team must do this while the Blue Team (defenders) try to stop them.
Although Red Teams use many of the same tools and techniques as they would in a pentest, they are being much more precise with their actions, using custom-built tooling to go low and slow and try to avoid detection by the Blue Team. Because of this, Red Team engagements typically last 3-6 months.
When to get a Red Team
Your organisation’s security strategy is quite mature, and you want to see what a real targeted attack on your organisation might look like, so you proactively prevent the real thing. You also want to test the capability of your Blue Team and your incident response plan.
When is it not a Red Team
Simply throwing together an internal pentest and some phishing isn’t really a Red Team, since this doesn’t properly simulate a real attacker. Not without prior thought on what the business objectives should be.
Vulnerability scans
Vulnerability scans are done by simply running a scanning tool like Tenable’s Nessus or Rapid7’s Nexpose. The output of the tool is then sometimes converted into a more understandable format. There is very little manual effort involved, and the results are what I would call “baseline”. Scanners simply aren’t very good at detecting anything but the most obvious vulnerabilities. For example, they will find if your Windows server is still vulnerable to Eternal Blue, but not if your Active Directory Certificate Services (ADCS) server is vulnerable, which it is by default.
“Automated Penetration Tests” go in this category as well. Despite the name, they are simply scanners that might have some specific logic programmed into them.
When to get a vuln scan
You want a quick, regular sanity check to make sure your infrastructure isn’t vulnerable to the most obvious vulnerabilities. Running a vulnerability scan every month or so is common practice. Don’t let this put you into a false sense of security, though. If you’re relying on scanners alone, you’re probably only getting about 5% coverage.
Vulnerability Assessment
Ask 10 people what a Vulnerability Assessment is, and you’ll get 9 different answers. Here’s ours!
A Vulnerability Assessment is a vulnerability scan with some additional manual effort. A consultant will look for vulnerabilities in a scope, but not exploit them. The risk rating given to these vulnerabilities is typically generic in nature, since without exploiting the vulnerability, you can’t know the impact. There is a good chance that false-positives will end up in the report since, again, without exploiting the vulnerability it can’t be verified.
Going back to pentesting for a moment, there is a misconception that the flow of testing goes something like:
- Enumeration - a fancy word for looking around the scope
- Vulnerability discovery - Find a vuln
- Exploitation - Take advantage of the vuln
In reality, it’s not so strictly sequential. We are often doing all 3 at the same time, and it’s not unusual to throw exploit payloads at a user input and discover a vulnerability because the system responded in an unusual way. What this means for Vulnerability Assessment is that a lot of vulnerabilities will be missed because exploitation is not done.
Isn’t it safer to not exploit vulnerabilities?
Technically, yes, it might be safer by a tiny margin. However, the risk of missing a critical vulnerability greatly outweighs any risk of exploitation. We use our experience to foresee when an action might cause negative impact to the system we’re testing. In those scenarios we either don’t do the action, or liaise with the client to do it out of hours.
When to get a vulnerability assessment
Honestly, never. The term itself is so ambiguous that you don’t know what you’re getting. It’s more expensive than a vulnerability scan and less valuable than a penetration test. It’s the worst of both sides. Ultimately, you’re left with just as much uncertainty after your assessment as before. Go with a pentest instead.
Bonus: Bug Bounty
We’ve done a whole other post about Bug Bounties vs. Penetration Testing, but in short, a Bug Bounty program allows external parties to submit vulnerabilities to you in exchange for a monetary reward. For example, check out our Vulnerability Disclosure Policy where we offer up to $1337 (and cookies 🍪).
Bug Bounties aren’t a replacement for penetration testing. They can be used in compliment with each other. For more details, check out our blog post above.
Still confused?
If you’re still not sure which service is right for you, that’s okay and normal. The best thing to do is reach out to a consultant who will take the time to understand your specific goals and recommend the right one accordingly. They should mould the service to your needs, and not the other way around. You can always rely on us for assistance, and a 30-minute call is always free. 🙂
Happy hacking!
About the author
Alexei Doudkine is Co-Founder and Offensive Director at Volkis. Hacker, tinkerer, car modder and dog person, Alexei has been in the infosec game for over 10 years focusing on the “attack” side of security. You can catch him on Twitter and LinkedIn.
If you need help with your security,
get in touch with Volkis.
Follow us on Twitter and
LinkedIn