
Posted on 2022-05-18 by Volkis in Business Security
Here’s the problem: technology is evolving rapidly, cloud adoption is at an all time high, development is faster than ever, infrastructure has become more dynamic, and security is struggling to keep up! The first step to regaining control: knowing what you have.
Let’s talk about it!
What is Attack Surface Management?
Before we dive into some examples, it’s important to understand the concept of Attack Surface Management. Attack Surface Management (ASM), also known as External Attack Surface Management (EASM) is a solution to the problem. ASM is the process of continuously monitoring and updating an inventory of an organisation’s online assets and accessible company information, then using the gathered information to guide security responses. The wider and more dynamic a company’s attack surface becomes, the more important it becomes to implement ASM. A good ASM program gives security teams the upper hand, enabling them to understand their own attack surface more deeply than attackers.
A good attack surface management program can be roughly split into 4 stages, as summarised by the image below.
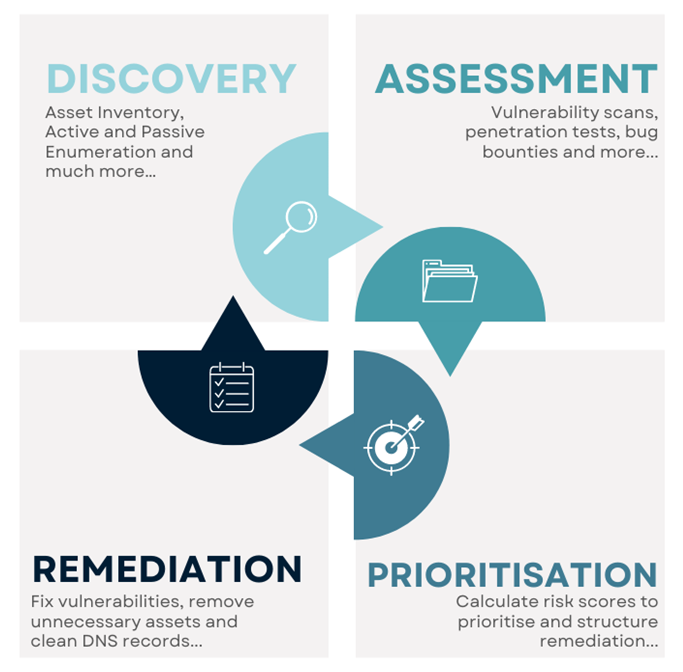
Why is ASM an emerging trend? 📈
The concept of ASM has been around for quite some time, but has recently gained a lot more attention, mostly due to three main factors, outlined below!
The Gartner Effect 🚀
Gartner (a large technological research and consulting firm) recently released a list of top security and risk management trends for 2022. Attack Surface Expansion was the first item on the list! Of course, the list is a result of what was already happening in the industry, but this report provided more concrete evidence of a trend that was previously only a feeling for many. The report was also pivotal because it informed many executives of the risks involved with attack surface expansion for the first time, and advised “Attack Surface Management” as the solution.
Bug Bounties 🐛
Bug bounties are an interesting subsector of cybersecurity because the incentive model is different to traditional security testing. Bug bounty hunters are paid for impact, while traditional security tests are paid for time and assurance. This means that creative research and solutions are organically encouraged in the bug bounty space through the incentive model. Some successful bug bounty hunters quickly discovered that there was money to be made by continuously monitoring a target’s external infrastructure for changes, and scanning regularly for vulnerabilities. Many bug bounty hunters ended up building out fairly advanced ASM systems for their own hunting, although ASM was not a term that was widely used at that time. The success of this method was seen by many, and also recognised by the security teams of many bug bounty programs.
At this point, many programs figured out that the only way to compete with the automation of bug bounty hunters was to “fight fire with fire”. It became clear that the attacker’s methods of building asset inventories of their company was working more effectively than their own, so they started to employ the same techniques as the attackers to regain an upper hand.
There are a few examples of bug bounty hunters who have ended up spinning their custom attack surface management solution into a full company (see Detectify, Assetnote and others!), renting it out to organisations who wish to improve their ASM capabilities.
Moving to the Cloud ☁️
The move to cloud infrastructure and cloud based tech has increased the need for ASM as an increasing number of many organisation’s assets are no longer self-hosted. Important data that was once stored in a private, internal network or even physically is now being stored online. This move is increasing organisations’ attack surfaces. Misconfiguration of these systems can create holes in the attack surface which may leave assets open to exploitation using relatively simple discovery tools. The adoption of cloud technology is allowing companies to improve their efficiency, speed and service; however this needs to be paired with adequate systems and processes to secure them.
Compliance
Organisations are also beginning to understand the compliance implications of not keeping track of their attack surface. There has been a growth in legislation and regulation regarding data protection that has given organisations the kick they’ve needed to protect their own assets and their customers - neglecting this can be severely detrimental to their business.
A Chilling Example - Storage Buckets 📃
If you’re unfamiliar with what a “storage bucket” is, you can basically think of it as online file storage. This type of storage is offered by all major cloud providers, typically with various security configuration options. Some buckets are meant to be public (for example, if they are hosting website files), others are meant to be private (for example, if they are a government department storing identity documents of citizens). In recent years, there have been troves of data breaches occurring due to misconfigured storage buckets.
Earlier this year, researchers at vpnMentor discovered a mistakenly public storage bucket belonging to Ghana’s National Service Secretariate (NSS) that contained a trove of unencrypted personal data on roughly 500,000 Ghanian graduates.
Around the same time, SEGA discovered an unsecured AWS S3 storage bucket containing multiple sets of AWS keys, MailChimp and Steam API keys, personal details of their customers and other details that would have allowed access to an internal notification service.
Also around the same time, the SafetyDetectives cybersecurity team said that they discovered an exposed S3 bucket belonging to Securitas, a European physical security company. This bucket contained about 3 terabytes of data dating back to 2018, including airport employee records.
All of these breaches (and many, many more!) happened just in January 2022. I know what you’re thinking - these would have been caught with a run-of-the-mill cloud security review! Here’s the thing though, they often aren’t. Many organisations, especially large ones, often have different cloud accounts split over different areas of the business, and use multiple different cloud providers. It’s not uncommon for entire segments of external infrastructure to be totally unknown to the security team because they have been spun up without the security team’s knowledge.
In any of these cases, it is paramount that the organisation utilises attacker methods to discover their own assets alongside their traditional methods.
Asset Inventory - Static 👉 Dynamic
There are varying methods to collect and update an organisation’s asset inventory. Asset inventory management can either be completed statically or dynamically. For smaller organisations, it may be possible, even preferable, to manually collect and manage your asset inventory; however as an organisation grows this is error prone and unscalable. In addition to this, the definition of an asset over recent years has changed and can now include data such as third party services, email addresses, code repositories and social media accounts. These types of assets are more obscure and may not be directly controlled or closely monitored by the organisation. These types of non-traditional assets may hold sensitive or useful information to an attacker. Dynamic asset inventory management is the process of using various tools to automate both the discovery of online assets and the continuous updating of inventories. Dynamic asset discovery has the benefit of being continuous and accurate. This means that security teams may become aware of new assets that have been created in a much shorter time frame, allowing for effective security responses.
Going beyond host discovery 🚀
Enumerating subdomains is not enough! The average hacker is equipped with a multitude of tools and techniques to enumerate an attack surface during the reconnaissance phase. Using both passive and active enumeration techniques, an attacker can collect vast amounts of data from an organisation’s attack surface which can be compiled and used to uncover vulnerabilities.
An attacker is not only looking to discover hostnames relating directly to an organisation, they also use more comprehensive Open-Source Intelligence (OSINT) techniques in their search for any information that will assist their pursuit to discover vulnerabilities within an organisations’ attack surface. Some of these techniques may include:
- Trawling historical password breaches
- Monitoring social media platforms such as LinkedIn for employee data
- Uncovering 3rd party services used by enumerating DNS records
- Searching GitHub for publicly exposed code repositories related to the organisation
By including comprehensive OSINT within the discovery phase of an ASM program, you can attempt to replicate the methods used by an attacker to provide a more comprehensive picture of the organisation’s attack surface. Combining this with the initial advantage of being internal, having host lists from cloud accounts, DNS hosts files etc. will help the organisation to regain the upper hand.
Conclusion
Today we live in a world where attack surfaces are complex, dynamic and ever changing. The relative ease at which an attacker can collect information about an organisation to identify their attack surface clearly demonstrates the importance of integrating ASM within security models.
To keep up with an ever-evolving threat landscape, it’s important to know what you have.
About the authors
Theo Bridgeman is a long-term terminal addict with a penchant for security. Luke Stephens is an ethical hacker and director of Haksec, a Volkis partner.
If you need help with your security,
get in touch with Volkis.
Follow us on Twitter and
LinkedIn