
Posted on 2022-04-05 by Volkis in Business Security
Our experience performing thousands of penetration tests has given us an in-depth understanding of common issues when engaging a consultant to complete a penetration test. We like to see our customers get the most possible value out of their penetration tests. Much of the responsibility lies with the penetration test provider, but cooperation and communication from our customers is also a key factor in the value that is provided.
In this article, we will be outlining some ways in which you, as an organisation receiving a penetration test, can get the most value for the money you are spending.
The image below depicts a summary of the main areas that will be covered in this post, including how to determine the best scope, how to identify an experienced consultant that suits your needs, how to prepare your systems and team, and how to communicate with the consultant effectively through all stages of the engagement and beyond.
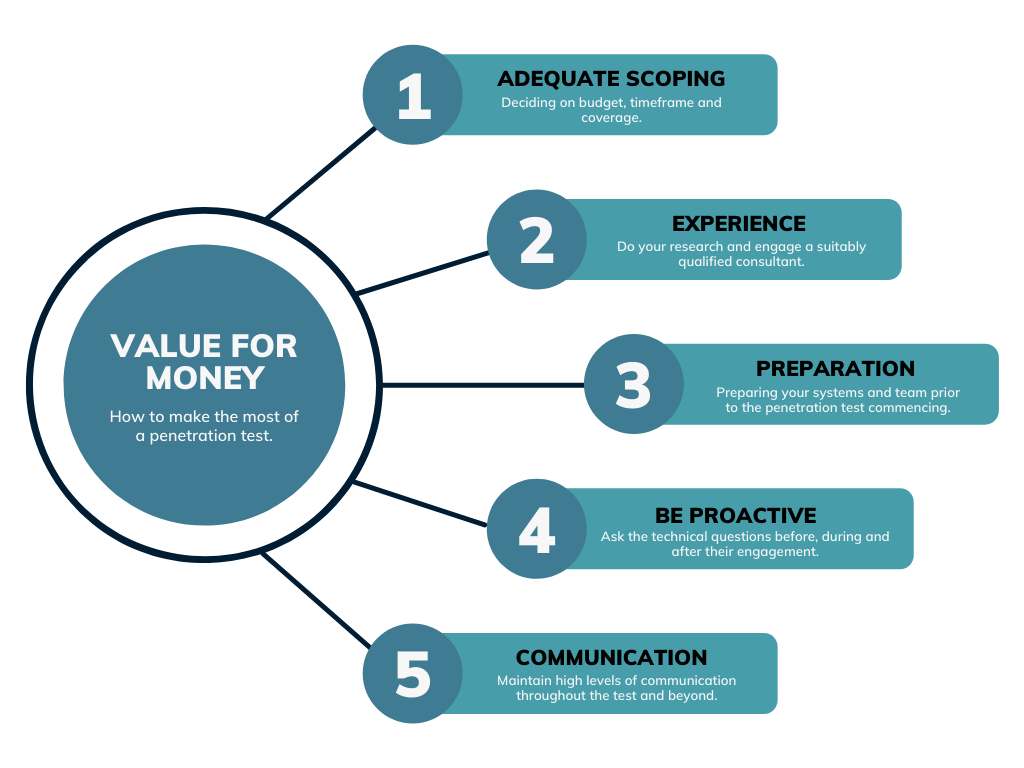
Deciding on Scope 🤔
Perhaps the most important part of getting the most out of your penetration test is deciding what you would like to have tested. There are many critical questions that need to be asked during the scoping phase. In many cases, deciding the scope will require input from multiple teams across the business to receive the best results.
Typically, the scope will be partially defined by real-world constraints - most commonly time and budget. For the ultimate security, it would always be best to test all hosts and applications. More often than not, this is not viable due to budget and time constraints. For this reason, it is important that we define a scope that provides the most amount of impact and coverage within our limitations.
Consider what the ideal outcome of the test is. Some questions you could ask yourself include:
- Are you aiming to generally uplift the security posture of your organisation?
- Are you wanting to ensure a specific product is secure before releasing it publicly?
- Are there specific business critical assets that you are concerned about?
Allow the answers to these questions define your scope. Focusing on specific assets in the scope will allow for greater testing depth in those areas, but reduces the overall coverage. In contrast, with greater coverage, the test will be able to span more assets, with less time being spent on business critical assets. It’s a balancing act!
Deciding the Visibility 👀
The visibility provided to the penetration tester is another important factor to consider during the scoping phase. Essentially, this is establishing the type of attack you are trying to emulate by determining how much prior knowledge and access the penetration tester is provided with before and during the test.
You can generally split penetration tests into three categories: blackbox, greybox and whitebox. The exact definitions of each are not widely agreed upon, but in general, blackbox tests provide no insider knowledge to the tester, whitebox tests provide in-depth knowledge of the target to the tester, and greybox is somewhere in between. These definitions are summarised in the image below.
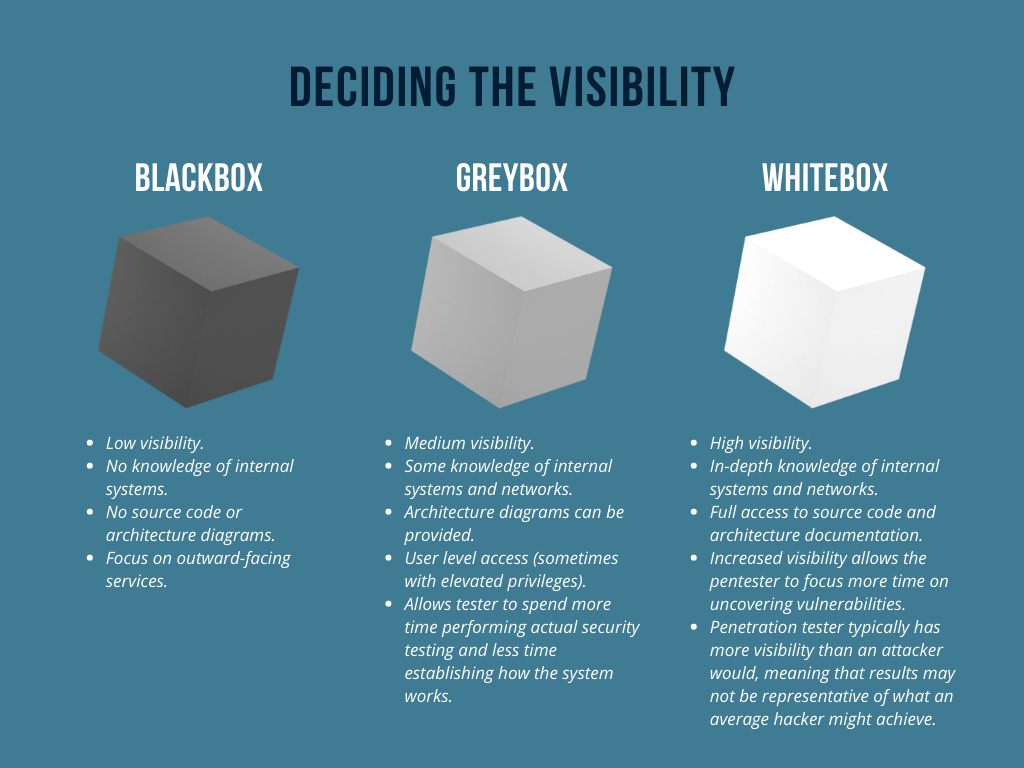
Blackbox Testing
Blackbox testing provides the lowest visibility to the penetration tester. It is meant to simulate a situation where the attacker has no prior knowledge of the system. This may be ideal for figuring out how the target might stand up to the average-hacker, however due to the time constraints of the penetration test, a large allocation of valuable time may be used figuring out how things work, what technologies are in use, what the source code might look like etc. Additionally, when a penetration tester has less visibility into the inner workings of the target, they are more likely to miss vulnerabilities. You may get more value from the penetration test by providing the penetration tester with more details at the start of the engagement.
Typically, we don’t recommend a blackbox approach since a large chunk of our time is spent finding things you already know about.
Greybox Testing
The next step up in visibility is Greybox testing. This is when the penetration tester is provided with some internal information, and perhaps a higher level of access to the application. Greybox testing is simulating an attacker that has a moderate level of knowledge about and/or access to the target. This allows the penetration tester to focus more time and effort on the actual security testing, and less time getting their bearings.
We generally recommend this approach. It allows us to have a thorough look at the scope and it negates some “security by obscurity” factors.
Whitebox Testing
The highest level of visibility is Whitebox testing. This is where the penetration tester is provided with a full understanding of the system, full access privileges, access to source code and design documentation. This allows for a comprehensive assessment of the target. One perceived downside is that the high level of visibility of Whitebox testing can influence the way the penetration tester behaves during the test as they are working with the limited information that is not available to hackers.
In general - we advise that it is better to provide full visibility to the penetration tester to uncover as many vulnerabilities as possible.
Onsite vs. Remote 🏠
Choosing whether the penetration test is completed onsite or remotely comes down to preference and company policy. Some companies have policies that do not allow remote access to their internal networks and therefore an onsite test may be the only option. In the vast majority of cases, penetration tests are able to be conducted completely remotely. In cases where the penetration tester requires access to an internal network, VPN access or a jumpbox may be utilised to provide access. An onsite test may be beneficial to organisations who wish to work closely with the penetration tester and help embrace the pentester as part of the team, which is why we prefer it to jumpboxes or VPNs. This is an important point that we’ll touch on soon.
Large companies will typically have a network spanning across multiple countries which might make remote testing the more logical choice. The adoption of remote working for many businesses as a result of the COVID-19 pandemic has allowed for a structural shift in business models away from the typical office-based arrangement. This is no different for penetration testing. Additionally, companies are now moving to cloud-based systems which have rendered onsite penetration tests less necessary because access to an external facing asset is the same whether onsite or remote. Remote tests also mean that a company does not have to rely on their local penetration testers and can engage a consultant from anywhere in the world.
Preparing Your Systems 💪
Good preparation of systems is paramount to getting the most out of your penetration test. Due to the nature of penetration testing, your servers may undergo unusual stress in many forms including:
- Increased traffic
- Increased junk in databases
- Excessive emails being sent (for example, password reset notification emails)
- Malicious payloads
In the worst cases, this may result in:
- Service downtime
- Broken systems
- Loss of account access
- Private data being exposed to the tester
It is important to prepare for these cases leading up to the penetration test, and plan for these cases occurring during the testing. If this were to happen in a production environment, it may cause inconvenient and costly outages, affect employee productivity and annoy customers. For this reason we recommend testing in a pre-production environment.
It is important that the system being tested contains dummy data, and that the application is fully usable in the same way that the production environment would be. For example, if the target was a web application that allowed users to generate invoices for their business, the ultimate environment to run a penetration test against would be a fully-functional pre-production environment with dummy users created, and dummy invoices created for each user, and credentials would be supplied for 2 users per role.
Firewalls can limit and even block the pentester and may require the tester to devote large amounts of time attempting to bypass them. Providing an ability to bypass firewalls will increase productivity and save valuable time during the test. For example, if the target is a web application, it may be worth whitelisting the penetration tester’s IP address or giving them direct access to the origin web server - remember, you’re testing the application, not the firewall.
For a more in-depth look at preparing for a penetration test, see our in-depth blog here.
Preparing Your Team 🧑🤝🧑
Let your team know that a penetration test will be going ahead so that your employees are aware that they may experience irregular activity for the duration of the test. This will also allow time for the security team to gather any questions they may have regarding the test before it commences.
A commonly overlooked barrier that is evident from a penetration tester’s perspective is a personal/cultural one. As the pentester is independent of/ external to the company, they will often be viewed by the security team as a threat. This type of negativity towards the test and tester can be detrimental. Embracing the penetration test for the greater good of the company and embedding the pentester as part of the team is critical to achieving the best results. No system or network is 100% secure which means that penetration tests are now an industry standard to improve system security. Encouraging your team that the penetration test is there to support them will be extremely beneficial for all parties. No punishment should arise from the results of a penetration test. The best results come from open, positive collaboration between the consultant and the internal team, working towards the same goal of improving the organisation’s security posture.
Questions to Ask Your Penetration Testing Provider ❓
Having questions prepared for the consultant is a great way to keep open lines of communication and get the most out of the penetration test. Here are a few examples of questions to ask.
- Do you foresee any issues with the engagement?
- Do you have all of the details that you need in order to complete this engagement?
- Have you checked that the access we have granted is sufficient for completing comprehensive testing?
- Do you feel that you provided full coverage on the application?
- What were the processes used and what was actually completed?
- Were all areas tested? If not, which areas were tested?
- Were there any areas that were not tested?
- Who will be conducting the penetration test? Can you provide a resumé?
- Do you offer retesting and is it included in the cost?
- How much of the cost is allocated to the retest?
- If it is not included, what is your pricing for retests?
- When do you usually schedule a retest?
For more tips on choosing a penetration testing provider, check out our blog “6 Things to Look For When Choosing Your Penetration Testing Provider”.
Proactive Questions ✅
Completing a penetration test should not be a matter of “They know what they’re doing, let them get on with it”. You are paying for the service, so make the most of having a security expert working for the company. The security consultant is there for you!
Make sure that you ask any questions that you might have about your organisation’s security. Ask questions before, during and after the engagement. Check in with the consultant during the test and discuss their findings. Once the test has been completed, your security team can ask for advice regarding how they might be able to fix any vulnerabilities that have been found and avoid them in future. Asking questions proactively about the test findings as well as advice about general security is key to making the most out of the money being spent to engage a consultant.
Of course, this works both ways! Many applications that we test are quite complex or specific to a particular industry. As such, it can take us some time to fully understand the target and the purpose of each feature. If someone at the organisation is available to answer questions about the target in a timely manner during the testing period, we will be able to provide more coverage. This is the one advantage we have over actual attackers!
Understanding the Report 🤯
Deciphering the report can be tricky at times. If you have any questions, don’t hesitate to contact your provider and ask them for clarification. The penetration tester should be happy to answer any questions about the report regardless of the time since the report was submitted. It is an expectation that the report is concise, detailed and easy to follow therefore if there are any areas that are unclear you are entitled to ask your provider to help elaborate on the report.
The penetration tester will be able to provide remediation advice if you’re struggling to understand the recommendations or are not sure of the specifics in a discovered vulnerability. Communicate with your team about the feasibility of any suggested fixes, if they are not feasible or relevant to your setup, be sure to ask the consultant for alternatives.
Retesting 🔄
Once your team has remediated the vulnerabilities, it’s worthwhile to complete a retest. Retesting is a fantastic way to see if remediation has been successful or the vulnerabilities are still present. There may be a workaround to your fix or the fix may not have worked at all. As the consultant has already completed a full penetration test on the system, a restesting report does not take as long, as they are more specific and the tester can target the areas where the vulnerabilities were originally identified. Retests are far less expensive than the original testing due to the specific requirement of retesting previously discovered vulnerabilities rather than finding new ones. If a large amount of vulnerabilities were discovered during the initial test then retesting will be able to give an insight into how effective the team has been in remediating them.
Communication is Key 🗣
As mentioned in every section, effective communication is the biggest contributor to making sure that you get the most out for your penetration test. Ensuring that proactive communication with the tester is maintained before, during and after the engagement, will allow you to get the best value for money for the test. Reputable penetration testing providers will always be able to advise you on how to best spend your budget to achieve the biggest impact.
Encouraging and ensuring your team that the consultant is there to help them is critical and will allow for valuable collaboration between your team and the tester. Proactive questions throughout the process will not only maximise the value for money of the penetration test but will also help your team to understand the vulnerabilities and allow them to implement fixes more efficiently with a greater chance of success.
About the authors
Theo Bridgeman is a long-term terminal addict with a penchant for security. Luke Stephens is an ethical hacker and director of Haksec, a Volkis partner.
If you need help with your security,
get in touch with Volkis.
Follow us on Twitter and
LinkedIn