
Posted on 2022-03-01 by Jessica Williams in Tools of the trade
Social media has become the platform that companies all over the world use to communicate with their customers, clients, critics, and investors. An attacker who gains access to an organisation’s social media accounts is able to send any message that they wish, posing as the organisation. Sending the wrong message on social media can cause a backlash, bad publicity, and in rare cases even be illegal as Elon Musk found out in 2018 when he was sued by the SEC over one of his tweets.
It is fairly common that an organisation will need to share access to their social media accounts, for example, to a marketing firm. Ensuring the keys to your social media account are well guarded is a great step towards protecting your brand’s image and reputation. In this blog, we’ll cover what can go wrong when managing social media account credentials, and how you can securely share access.
The First Step: Choose a Strong Password
Occasionally, data breaches occur where usernames/emails and passwords are publicly exposed. In these situations, the passwords are typically dumped in an encrypted format. When this happens, it is extremely important that the password you have chosen is strong - otherwise an attacker who gets their hands on the data may easily decrypt your password and use it to log in to your account. “Cracking” is the process of attempting to decrypt the password by brute forcing billions of different passwords. Let’s have a look at what it takes to “crack” a password.
As a simplified example, imagine you have a password that is a number between 1 and 9. If I have 3 guesses to find your password on average I will be right 30% of the time, which is very bad for securing anything! Modern passwords are much more complex but attackers also get a lot more guesses, a relatively powerful computer can guess billions of passwords per second. The biggest factor in password strength is length. Longer passwords require many more guesses to correctly guess. To illustrate this point, let’s have a look at an example below.
| Password | Time to Crack |
|---|---|
| social | 77 milliseconds |
| social media | 3 hours |
| social media is | 99 days |
| social media is cool | 5,200 years |
This example shows how length can affect the security of a password but these are just estimates. In the real world this password could potentially be cracked a lot quicker because it is just four normal English words joined together in a predictable sentence. These are still vulnerable to dictionary attacks, where an attacker uses a large word list to brute-force passwords. In the next example, we’ll look at the next important factor, complexity, and how adding a wider variety of characters to your password can increase the potential time it takes to crack it.
All of the passwords below are 10 characters each. With each password, a new type of character is added to the combination. We can see that the time to crack the password quickly becomes practically impossible to crack.
| Password | Type | Time to Crack |
|---|---|---|
| 6536947254 | Numeric | 1 day |
| v5g537tjis | Alphanumeric (lowercase) | 1 year |
| gEdsuHDp8g | Alphanumeric | 1,800 years |
| WXe2b$rCe@ | Alphanumeric + special | 10,000,000 years |
For our final example let’s look at two passwords with cracking times in the billions of years! The first example also uses words but is a little more complex and is far easier to remember than the second one. This type of password that contains a string of words in a random order is commonly called a passphrase and its benefits will become more clear in the next section.
| Password | Time to Crack |
|---|---|
| guacamole entraps all consumers | 3,328,312,900 years |
| x!x!SJBF9aXP64 | 2,398,209,300 years |
If you want to know more about cracking passwords, check our other blog post!
So you have a secure password, what else could go wrong?
Having a complex password or long passphrases is a really great way to secure your online accounts but won’t help you in some situations. Let’s look at a few different ways that your passwords can get into the hands of attackers.
Leaks
In the last section we looked at the difference between a passphrase and a password. The passphrase was much easier to remember. The property of memorability is very useful because it means that the password is less likely to be written down somewhere or stored in a place that another person could access. When a password is obtained by somebody else without coercion this is called a leak. Similar language is used in journalism when sensitive information is revealed by a source voluntarily. Another common instance of leaking passwords is when they are written down somewhere and accidentally photographed. This happened to the Hawaii Emergency Management Agency in 2018 when a photographer from the Associated Press shared a photo taken in the office where a sticky note can be seen with a password written down.
Breaches
In contrast to leaking, breaches happen when sensitive information is obtained via malicious means such as hacking. Online applications store user credentials in a database, which is a system for organising and accessing data, kind of similar to a spreadsheet. When developers are building databases they can sometimes make mistakes, even accidentally publishing these databases onto the internet where hackers can find them and examine the credentials stored in them. Hackers can also exploit vulnerabilities to gain access to these credentials.
In most cases, it’s not the responsibility of the user to protect themselves from a breach. The responsibility users have in this situation is to mitigate the damage that a breach may cause by using unique, secure passwords on each website so that if for example, a breach happens on Twitter, their Facebook account is still secure.
You can check if your information is included in any known breaches by visiting the website “Have I Been Pwned” (https://haveibeenpwned.com/)
Phishing
“Phishing” is a technique of baiting fish (a derogatory term used in poker that means stupid or gullible) to trick users into providing their passwords. When phishing is talked about online it is usually referring to a social engineering attack where an attacker normally pretends to be an official representative of some organisation and asks for sensitive information like login credentials, bank details, or the information of another person. When online it is exceptionally rare for any organisation to require you to send them your login credentials. If this happens you should immediately be suspicious of this person’s motives and absolutely verify their identity before telling them anything. If you wouldn’t tell it to a stranger don’t share it online!
Password Managers
One of the best ways to create, store, manage and share credentials is to use a reputable password manager. A password manager is a tool that generates and stores credentials in a secure software platform. You can create one strong password to secure the password manager and every other password is created and stored in the platform. This has several benefits, the main one being that passwords are not reused across multiple services, reducing your risk if one service you use gets breached. Another great feature is that passwords can be safely shared with your team. Instead of sending somebody the actual username and password for a service, you share the password inside the password manager, and the person you share it with can go and retrieve the details themselves. Some password managers also check your accounts for known breaches and alert you if one of your credentials becomes public.
Here is a quick tutorial to get you set up with a password manager, called BitWarden. There are tons of great password managers out there like Dashlane, 1password, and KeePass but for the purpose of showing you how to get setup quickly, we’ll demo setting up BitWarden in Chrome:
Firstly, create an account and download BitWarden from https://bitwarden.com/download/. We’ll download the web browser extension:
Once it’s installed, select the extension in the top right corner of your browser and login:

Next, select the “+” symbol in the top right:
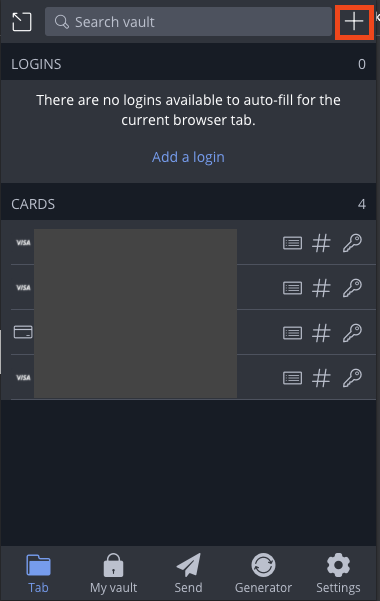
Fill in a name for the credentials and your username, then select the circle to generate a password:
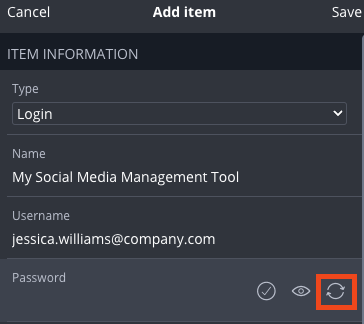
This will bring you to a password generator, where you can choose different options like a password or a passphrase. We’ll create a passphrase and increase the number of words to 4 and include numbers:
This password would take 68 decillion years to crack, according to How Secure Is My Password!
Click save and set this password in your social media management tool.
Multi Factor Authentication
MFA, also known as two-factor authentication (2FA) adds another layer of security onto your accounts online. In addition to providing a username and password when you log in you will be required to provide a temporary code as well. Codes can be generated in several ways; they can be sent to your email address, texted to you, generated by an app, or stored on a hardware device like an RSA fob or a Yubikey. The benefit of MFA is that even if an attacker knows your username and password they won’t be able to log in without the additional code that changes frequently. If somebody does try to log in without this code, platforms can alert you that a login was attempted and you can take steps to replace any passwords that may have been leaked.
Social Media Management Tools
Normally when working in marketing or any role where you’re managing social media or online marketing platforms, multiple people will need access. Without a social media management tool, like Loomly, Hootsuite, or Buffer, generally marketing teams will have to share one account. This can lead to problems like:
- How do you manage different roles? How will you ensure the intern can only create drafts for approval and posts won’t be accidentally sent straight to the public?
- How do you know who posted the content? What if a rogue employee posts sensitive information online, how do you identify the culprit?
- How do you ensure you’ve properly revoked access when an employee leaves the company?
There is a very important concept in Cyber Security called the “Principle of Least Privilege”. It basically means that people should only be given the privileges needed to complete a task. For example, the intern likely doesn’t need the ability to delete a social media account. So by the principle of least privilege, they should not even have access to that function. Using a good social media management tool will help you to implement this through roles and permissions.
An example of roles and permissions you might use would be:
- Editor: Somebody with full permissions for content management but no access to managing the account itself, so they wouldn’t be able to delete a social media account.
- Contributor: Somebody who can create, edit, and view posts but cannot actually post the content to an account.
- Viewer: Somebody who can comment on draft posts but cannot create, edit or delete them.
Social media platforms typically do not allow this kind of granularity of permissions, but social media management platforms do. Not only is this an excellent addition for security, it is also just an easier way for multiple people (such as a marketing team) to manage social media accounts. It’s not often that implementing additional security controls actually makes things more convenient!
Some social media management tools, such as Loomly, also allow custom approval workflows to be created. This makes it impossible for a single rogue employee to post damaging content to social media profiles, even if they have an account on your social media management tool, because you can create approval gates.
As an example, you may set up a custom workflow where your junior social media manager is able to create and schedule posts but they will not ever be actually posted to your social accounts without first receiving approval from two senior managers.
Using a social media management tool also provides good ways to manage some other tricky situations, for example:
| Situation | Solution |
|---|---|
| Someone who once required access to your social media accounts no longer does - for example, because they have switched jobs. | Remove their account from the Social Media Management tool |
| Your social media manager’s account was hacked. | Reset the password. (If this was a social media account being hacked, you may never get the account back!) |
| A damaging, malicious post appears on one of the company’s social media accounts. | As an administrator, you can login and delete the post. Then you can look through the logs to attribute which account the post was created from. |
The Low-Down
The ultimate way to securely share access to your social media accounts is:
- Ensure that your social media accounts have a strong, unique password
- Ensure that your social media accounts are protected with 2 factor authentication
- Connect your social media accounts with a management tool such as HootSuite, Loomly or Buffer
- When someone requires access to your social accounts, create an account for them within the social media management tool, ensure that they use multi-factor authentication and a strong, unique password
- Use the principle of least privilege to assign user roles for each account within the social media management tool, set up approval gates
We hope this post can help you to manage your social media accounts securely and prevent any security incidents that may damage the reputation of your brand. It really doesn’t take much time to set up these controls and will be well worth the effort!
About the author
Jess Williams is a Montreal-based security specialist, previously from Brisbane, Australia. She’s currently working in DFIR in the mining industry and has experience in penetration testing and technical writing. She’s passionate about creating engaging content and knowledge sharing both in and outside of the Cyber Security industry. You can catch her on Twitter and LinkedIn.
If you need help with your security,
get in touch with Volkis.
Follow us on Twitter and
LinkedIn